Cyber Insurance Checklist: 12 Essential Security Controls
Do you want to equip yourself with the knowledge necessary to succeed in the Information Security job market. This screenshot depicts the final warning before Android factory resets the device. Becoming a cybersecurity analyst offers a rewarding career path. System andInformationIntegrity SI 2,SI 4, SI https://cyberinsurecheck.com/ 5. Astra also conducts a gap analysis of an organization’s security systems to find the gaps in security and performance that can be improved on. This blog post breaks down each of these elements and offers advice for streamlining existing compliance functions to create a more effective and efficient CMS. Auke Vleerstraat 6D7521 PG EnschedeNetherlands +31 53 750 3070. Obviously, companies should make it a priority to seek out a cloud security company that will best help them meet their responsibilities for securing their cloud based infrastructure. Competitive forces and a lack of catastrophic events in prior periods led to lower cedent retentions and loosened up terms and conditions. Are there other features a facial recognition software should include. Editorial comments: Amazon Rekognition can be used by organizations that have zero machine learning expertise. Consider these cybersecurity facts. Such address or hyperlink including addresses or hyperlinks to website material of Morgan Stanley Wealth Management is provided solely for your convenience and information and the content of the linked site does not in any way form part of this document. McAfee is a trusted name in the cybersecurity landscape, offering a wide range of antivirus and security solutions.
Download Product Flyer
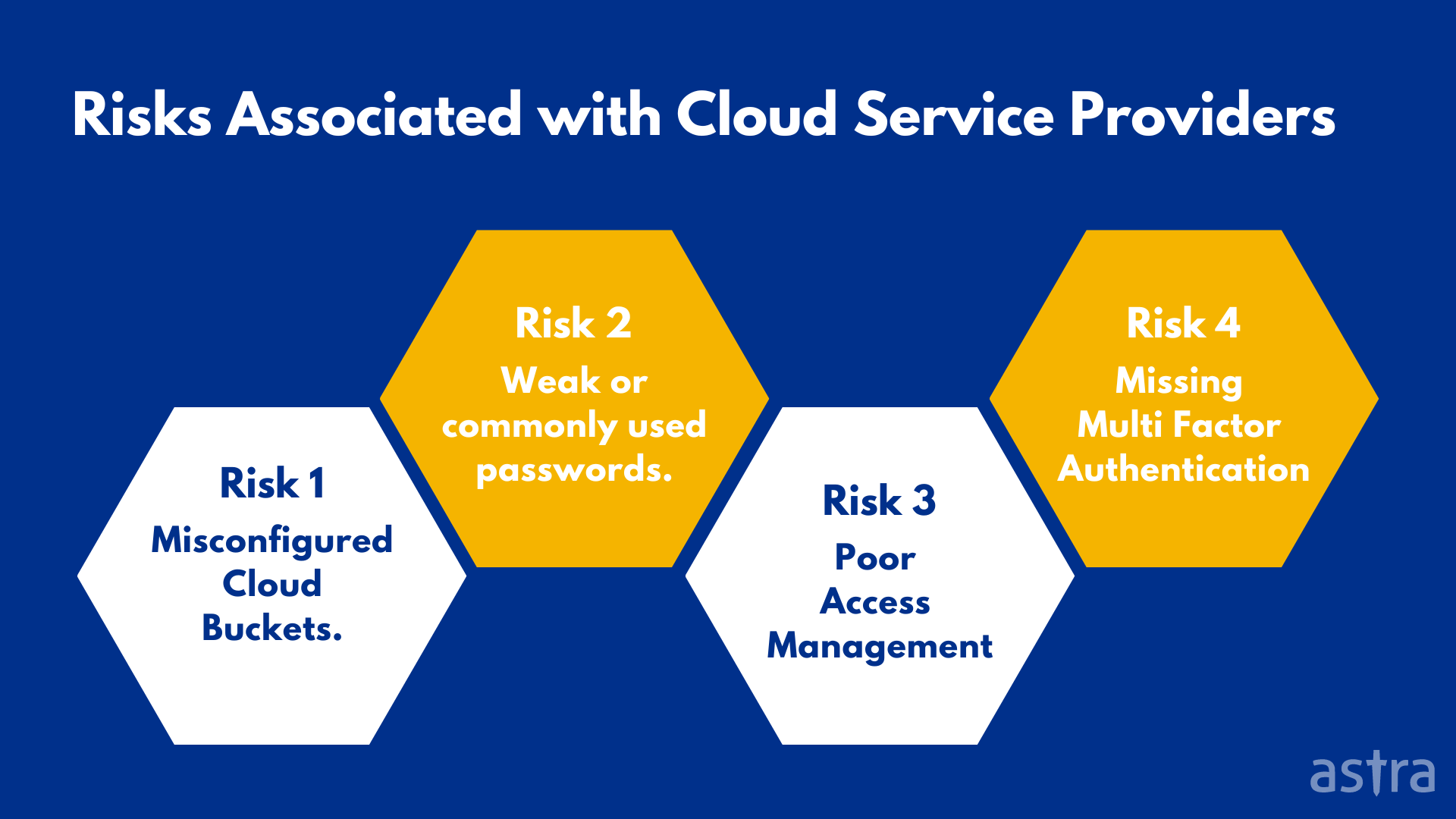
What a DevOps Post Graduate Certification From Caltech CTME and Simplilearn Means for You. Each organization can then opt to add in any of the remaining four Trust Services Criteria TSCs — Availability, Confidentiality, Processing Integrity, and/or Privacy — depending on their type of business, organizational goals, or customer/ partner demands. “Poor compliance management can have huge consequences for a financial institution including enforcement actions, fines, and bad publicity. Management Environment. 4 Create Your Disaster Recovery and Business Continuity Plan 298. Systems track the location of data and who is accessing it. Standout features and integrations. By gaining a more detailed and holistic view of the threat landscape, companies can more quickly understand threats and take steps to shut them down. Weak, compromised, or reused passwords are the leading reason for data breaches and other types of cyber incidents.
Editors
NIST SP 800 171 Revision 2, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations. Options for limiting data use. GoodFirms is here to aid you with a list of cloud computing security service providers that you may hire. Over the last decade, they have paid out tens of millions of dollars in claims. However, the idea that there is a cybersecurity industry “bubble” that will one day burst seems almost ludicrous against the backdrop of nonstop cyberattacks impacting governments, nonprofits and companies great and small across all industries. Netskope specializes in SASE, CASB, and SD WAN technology. Most cyber insurance companies usually do not cover criminal investigation costs. He’s also a Cyber Zero Trust Strategist and Evangelist and Chief Trust Officer. These reports can also help with internal auditing and compliance with security standards. Download these attachments only if you are sure that it is a legitimate email. 1Installation ofSoftware onOperational Systems. PR CDA 001 CyberDefense Analyst. The second is to promote the development and utilisation of data assets. Gen Digital is a multinational software company co headquartered in Tempe, Arizona and Prague, Czech Republic. Its cutting edge technology and intelligence driven approach helps organisations identify and respond to advanced attacks effectively. Twenty percent of exam objectives for CompTIA CySA+ CS0 003 were updated to include cloud and mobile, current trends and threat intelligence. Update existing plan of action and milestones basedon the findings from control assessments, impactanalyses, and continuous monitoring activities. Identity and Access Management IAM is a framework of business processes, policies, and technologies to manage electronic or digital identities. The CSF is used widely internationally; Versions 1. In this Talk, our guest is Daniel J. The firm’s cybersecurity experts and advisors offer a wide range of services, including data encryption, file integrity monitoring and automated malware detection – complemented by 24/7 support. The book covers cyber warfare, detailing the covert operation that led to the deployment of the world’s first digital weapon. OV SPP 002Cyber Policy andStrategy Planner. Detailed information about the use of cookies on this website is available by clicking on more information. Footnote 17 In some cases, cyber security measures underpin critical infrastructure that protects data, thereby safeguarding personal information. Department of Homeland Security DHS, “DHS Study on Mobile Device Security,” April 2017. Protecting over 100,000 organisations of all sizes, according to the company its solutions protect customers from 5th generation cyber attacks with an industry leading catch rate of malware, ransomware and other types of attacks. Quantum Computing Security. Palo Alto Networks is a global cybersecurity company that provides a range of network security products, ensuring visibility and control over network traffic.
5 Filter content
By using a cloud based architecture, the threat detection and prevention can be supported at mass scale across the network, endpoint and cloud. Two years ago, WannaCry ransomware encrypted millions of computers. However, it usually pays for itself with bottom line enhancements. Certificate operationand configuration arecontinuously monitored. Mimecast provides multi layered security, ensuring every email system, whether inbound or outbound, is scanned and safe. OV LGA 002PrivacyOfficer/PrivacyCompliance Manager. Nisos operates a multi source managed and intelligence system, which supplies active technology defenses. In fact, some carriers are inserting cyber exclusions into these policies to protect themselves further. System andInformationIntegrity SI 4. SOC 2: What’s involved. With its robust product lineup and long standing industry presence, Cisco remains a reliable choice for organizations looking to bolster their IT and cybersecurity posture. After registration, whenever a user logs in, the system first verifies their identity through the username, which could be an ID number, pin, or card, that they provided at the time of registration. An entity inside the security perimeter that is authorized to access system resources but uses them in a way not approved by those who granted the authorization. Best for: Privacy Compliance, Data Governance, B2B Security. To this end, China has generally sought to conform to global norms, confining its more aggressive international behavior in cyberspace to activities seen as part of spy games – such as cyber enabled espionage and influence operations – rather than in perceived “rogue” activity, such as infrastructure disruption.

JumpCloud
Using a smartphone camera, it recognises relevant images and real world objects. Every software has its pros and cons, but these are the main factors we took into consideration before settling on this list. We do not recommend this program to past participants of Cybersecurity for Managers: A Playbook unless you are looking for a refresher. They plan ahead based on past experience, trends in the market, and your own insecurities. 90 to be awarded an LL. CEH – Certified Ethical Hacker: A certified and skilled individual who knows how to look for vulnerabilities and weaknesses in systems using the same tools as a bad actor would. New capabilities included the ability for the Dragos Platform to leverage data from CrowdStrike’s Falcon Insight for IoT offering. Bm, the leading publisher of news, data and insight for the catastrophe bond, insurance linked securities, reinsurance convergence, longevity risk transfer and weather risk management sectors. What Is the Projected Job Growth. You’ll learn all about e mail and Web based forensics, mobile forensics, passwords and encryption, and other e evidence found through VoIP, voicemail, legacy mainframes, and databases. Cybersecurity and Machine Learning Engineer. Nov 7, 2023 1 min read. In fact, this book is different in many aspects from every othergeneral AI book you may have seen before. You can update your choices at any time in your settings. Dec 27, 2023 6 min read. Cisco provides a solution for IT, networking, and cybersecurity. These are the foundational elements. It serves as an essential utility for developers and operations teams to maintain application health and performance. Their unique blend of contextual threat analysis and rapid data collection encompasses users, assets, services, and networks, simplifying the often complex terrain of compliance and risk management. To learn how your data will be used, please see our privacy notice. Broadly speaking, the security principleenforces the protection ofdata and systems, against unauthorized access. Unjustified espionage may also be a just cause for offensive counterintelligence. Gen safeguards users against advanced online threats, bringing award winning cybersecurity, privacy, and identity protection to nearly 500 million users. Our signature red boxes are architected to be the industry’s smartest, fastest, and meanest security devices with every scanning engine running at full throttle. This very capability is why I believe it’s “Best for advanced threat protection,” providing users an assured defense against sophisticated email based attacks.

Is SOC 2 a certification or attestation? Why it’s important to get right
SIEM security information and event management is software that helps organizations recognize and address potential security threats and vulnerabilities before they can disrupt business operations. This function assists in developing an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities. With no hardware components, it can be easily deployed and integrates seamlessly into existing hybrid cloud environments. On top of this, advances in technology have made cybercrime more accessible than ever. Whether it’s an internal solution or one offered by a third party provider, make sure any CMS software implemented includes these seven features. Mobile Services Category Team MSCT, “Device Procurement and Management Guidance,” November 2016. On the bright side, even with expensive cyber insurance costs, 3% of issuers intended to buy less coverage in 2023 than in 2022. At best, your organization will potentially miss out on building business value. A VPN virtual private network conceals your IP internet protocol address and web activity, preventing bad actors from accessing your location and seeing your browsing history. Of course the following lists aren’t complete, but they should provide food for thought and underscore the importance of understanding how to cybersecure yourself and your loved ones. With a network that has paid over $230 million in bounties, HackerOne boasts an impressive clientele including major corporations, tech giants, and government agencies. Verified purchase: YesCondition: NewSold by: loperbayhbw. Technologically speaking, every company is unique in one way or another. This technology can be used by various businesses and organizations to reduce the danger of identity theft significantly.

The country you have selected will result in the following:
To view or add a comment, sign in. With cloud hosted applications becoming a mainstay in today’s world of IT. It’s a cloud based solution that converges network and security functionalities. National Institute of Standards and Technology NIST Special Publication SP 800 30 Revision 1, Guide for Conducting Risk Assessments, states that riskis “a measure of the extent to which an entity is threatened by a potential circumstance or event, and typically a function of: i the adverse impacts thatwould arise if the circumstance or event occurs; and ii the likelihood of occurrence. Risk assessment assumptions and constraints were developed using a NIST SP 800 30 Revision 1 Generic Risk Model as shown in Figure F‑2. An architecture contains descriptions of all the components of a selected, acceptable solution while allowing certain details of specific components to be variable to satisfy related constraints e. Protecting over 100,000 organisations of all sizes, according to the company its solutions protect customers from 5th generation cyber attacks with an industry leading catch rate of malware, ransomware and other types of attacks. For a claim, the reinsurer bears a portion of the losses based on a pre negotiated percentage. Administrations gain precise controls, eliminating unauthorized and excessive access permissions, mitigating risk, and reducing the overall attack surface. Data security is particularly important for enterprises, as they typically have access to a larger volume of sensitive data, including sensitive customer data, company data, and intellectual property. The worldwide coverage includes. Each of the five Categories includes numerous Trust Services Criteria, which are the specific criteria used to assess a service organization’s environment. Key features include convergence through a unified operating system, acceleration with patented ASIC architecture for improved performance with reduced power consumption, and AI/ML security with FortiGuard global threat intelligence for automated protection against known and unknown threats. The act recognized the importance of information security to the economic and national security interests of the United States. Identify the location of and the specificsystem components on which the informationresides;b. However, recently, the app has introduced the Public Figure Facial Recognition feature. Privacy practices may vary, for example, based on the features you use or your age. Detect internal and external threats across your entire network, with cloud delivered analytics. With a team of highly skilled and experienced professionals, Rivell. Other services include email security, endpoint security, and security management. Enter cybersecurity contests to test yourself and identify where you need improvement. These are discussed in order from the least amount of training needed to the most amount of education required below.
Up next
While exact prices can fluctuate and depend on specific deals or packages, tools like Netskope and Zscaler often have competitive starting prices. Network Rail discusses how it is using data to reduce the need for speed restrictions and lower the risk of delays for the. The following provide an overview of the mobile deployment components involved in the original current Orvilia architecture. 8 Net asset value used for total shareholders’ funds. Proponents of big data analysis have claimed that it could play a key role in helping detect cyber threats at an early stage by using sophisticated pattern analysis and combining and analyzing multiple data sources. 👉 Built In Dashboards and Notifications: We prefer software that can give you a 360 degree view of your data and notify you when something’s amiss. Learn more about an LLM in National Security and Cybersecurity Law. Customers entrust their personal and financial information to organizations and expect that it will be kept safe from cybercriminals. In addition to its product lineup, Trend Micro offers consultancy and managed services through its TrendLabs division to help businesses increase their security posture. For example, it is now easier to buy malware from the dark web meaning that people with very little technical skill are able to orchestrate advanced attacks. Standout features and integrations. Tips for selling Cyber Insurance.
How Clearview AI Helped Shape the War in Ukraine
Underlying concepts are explained with clearanalogies and accessible language. Customer base: This solution caters to companies that need e identification and e signing. Procedures to facilitate the implementation ofthe system and services acquisition policy and theassociated system and services acquisitioncontrols;b. Provide a support point of contact. Your accelerated course includes. Research Information and Knowledge Hub for additional information on IMD publications. You can watch the EDPS Supervisor’s address at the European Parliament’s Cyber Days here. True cloud security is not about taking the existing architecture and virtualizing it in the cloud. Understanding what SOC 2 compliance requires and putting the proper safeguards in place can help protect your data while maintaining peace of mind. Congratulations – you’ve come to the right place. In addition to the company’s Live Cyber Threat Map, which displays security updates in real time, Check Point products cover network security, endpoint threat protection and cloud and mobile security. Intrusion detection and prevention systems IDPS and security information and event management SIEM solutions can be used for identifying suspicious activities and potential threats in real time. To enable an organization to focus and prioritize its efforts, consistent with its risk management strategy and business needs, this function stressed the importance of understanding the business context, the resources that support critical functions, and the related cybersecurity risks. Nov 7, 2023 1 min read. Information Systems Security Officer. QAwerk security team combines the power of the latest cybersecurity tools with its solid pen testing expertise to unearth the most impactful exploits. It was initially developed to recognise everyday objects. Key updates from Ivanti have included a partnership with mobile security firm Lookout, which has brought improved mobile threat defense to the Ivanti Neurons platform. “Poor compliance management can have huge consequences for a financial institution including enforcement actions, fines, and bad publicity. That’s why its official title is the Framework for Improving Critical Infrastructure Cybersecurity. The backups capability is used to take backups of the Active Directory configuration. CISSP – Certified Information Systems Security Professional: This certification covers the fundamentals of cybersecurity. Dec 21, 2023 2 min read. IAMsystems help enforce access control, which is fundamental to the security,confidentiality, and privacy principles of SOC 2. If an employee’s clock in photo does not match their reference photo, the software is quick to notify admins by email and highlight the error on the employee’s timesheet. Dummies helps everyone be more knowledgeable and confident in applying what they know. Whether you’re a cybеrsеcurity еnthusiast, a businеss ownеr, or somеonе еyеing a carееr in this dynamic fiеld, this piece is your compass to thе bеst in thе businеss and thе innovations that will shapе thе futurе оf cybеr dеfеncе. Find out here what it means to be secure by design and secure by default. This included social websites like Facebook and YouTube. Management and staff should receive training that reinforces and helps implement the financial institution’s written policies and procedures.
Working Together with Partners for Customer Success
NAVTECH a vanguard in digital transformation and bespoke software solutions, empowers businesses with state of the art technology. David points out that HYAS’ flagship product, HYAS Protect, monitors outgoing DNS activity and detects anomalous patterns, so security teams can identify digital exhaust before cybercriminals have a chance to cause damage. Big Blue NYSE: IBM earns mention for unified endpoint management UEM, SOAR, SIEM, encryption, database security, threat intelligence platform, single sign on, and managed security service providers MSSPs. On 11/9/2020, the OCC published their fall 2020 edition of the publication, Semiannual Risk Perspective. The modifications to the Security, Privacy, Breach Notification, and Enforcement Rules were intended to enhance confidentiality for PHI and security in data sharing with regard again to protected health information. Osano is a powerful solution, but like all entries in this list, its drawbacks must be weighed against its benefits. They are crucial in maintaining ongoing compliance and identifying potential compliance risks. Cybersecurity is a growing concern across the world, with criminals targeting businesses of all shapes and sizes across industries. We consider some of the leading CISOs within the EMEA region who are committed to developing and implementing security policies to protect critical data. To learn more about the threats that Check Point solutions can help to protect against, check out the Check Point cyber security report. The goal of ESM is to enable enterprises to gain better control over a distributed and complex enterprise environment. In fact, well before OpenAI opened the floodgates with ChatGPT almost a year ago, Gartner forecasted the worldwide AI software market would top $135 billion by 2025. Location: San Francisco, California. I’d love to hear about it. Platform and key solutions. Timekeeping web application. Facial recognition software FRS is a biometric software that matches faces in images to an existing database of identities using AI and ML. 1 in 2018, stakeholders have provided feedback that the CSF needed to be updated. Complete Staff Awareness E learning Suite. ENTERPRISE ARCHITECTUREControl: Develop an enterprise architecture withconsideration for information security, privacy,and the resulting risk to organizationaloperations and assets, individuals, otherorganizations, and the Nation. The thirdsection emphasizes the role of knowledge in decision making andpresents an array of methods for representing and reasoning withlogical or categorical knowledge. Advise employees to back up the personal data maintained on devices. First, let’s take a step back and list the cybersecurity issues that are probably top of mind. Each facial recognition software provider focuses on different aspects of the technology layers to provide almost flawless service. Pricing: As per the online reviews, the price for the Network Security appliance starts at $10968. Palo Alto Networks is a pioneer in cloud security, providing next generation firewall and cloud native security solutions to protect organizations’ cloud infrastructure and applications. Sounds good so far, right. Please check the box if you want to proceed. Orvilia examined the sample tables in NIST SP 800 30 Revision 1—Tables E 1, E 2, E 3, E 4, and E 5—and analyzed the sources of mobile threats identified in Task1 4.
HIPAA
On January 17, 2013, the Department of Health and Human Services’ “HHS'” Office for Civil Rights “OCR” released its long anticipated megarule “Omnibus Rule” amending the HIPAA Privacy, Security, Breach Notification and Enforcement Rules. Licensing for Prisma Cloud is a little unusual, but not overly complex. You choose the length of your audit window depending on how long your controls are in operation. However, any third party could become an enterprise cybersecurity problem. This cybersecurity firm holds CREST certification, a testament to its exceptional expertise and professionalism. Table 1 Mapping the Recommended Best Practices for TLS Server Certificate Management to the CybersecurityFramework. A physical firewall device or firewall hardware is an appliance that sits in between the uplink and the client system and filters what traffic gets through based on pre configured security policies, user profiles, and business rules. The Venafi Machine Identity Protection platform used in the exampleimplementation described in this practice guide. Two factor authentication. Duo Security makes two factor authentication software for cloud security. This includes assessing vulnerabilities in hardware, software, network infrastructure, and human factors. IT AuditManagement Software. Discover the latest in global technology and connectivity at MWC Barcelona 2024, where industry giants converge to discuss 5G, AI and more industry trends. Pricing: The Company offers a comprehensive suite of solutions at varying rates. Pricing: Indusface offers AppTrana with two pricing plans, Premium $399 per app per month and Advance $99 per app per month. Share sensitive information only on official, secure websites. Location: Fully Remote. A security protocol providing privacy and data integrity between two communicating applications. Netgate staff can help you implement effective solutions to solve those problems. In the current online text based era, acronyms and definitions comprise a large portion of our lingo. Yet another leading cybersecurity provider, Zscaler provides users with a tight zero trust security posture that can be managed at all aspects, thus making navigation easy and the security posture more secure. The cost of recovering from identity theft is included in credit card monitoring and ID theft repair coverage. Many institutions already have a strong CMS in place. What makes them recognisable. It also secures resources like cloud applications, web services, and applications. Cybersecurity analysts and cybersecurity engineers both play vital roles in safeguarding an organization’s digital assets, but they have distinct focuses and responsibilities within the realm of cybersecurity. “Easy to connect and follow on distance. Faced with these mounting risks, the mobile industry, companies and app developers have a heightened responsibility to ensure the safety of the platforms and the backend systems, where so much personal information is collected, handled and stored.